GSS News & Information

Why Your Physical Security Systems Are Your Biggest Cyber Vulnerability
Cybersecurity Awareness Month 2025: Why Your Physical Security Systems Are Your Biggest Cyber Vulnerability By Scott Gordon | Gordon Security Solutions October marks Cybersecurity Awareness Month, with the Cybersecurity and Infrastructure Security Agency (CISA)...
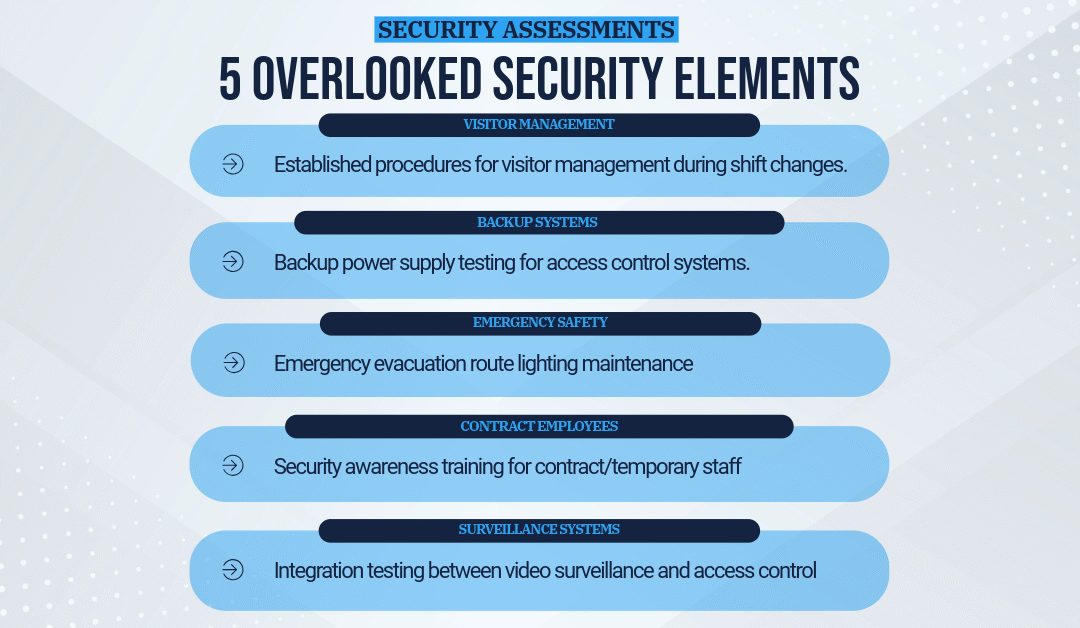
5 Often-overlooked elements in physical security assessments
Introduction Most security assessments focus on the obvious elements - access control systems, video surveillance, perimeter fencing, and intrusion detection. These are critical components and rightfully receive significant attention. However, working with security...
GLOBAL SECURITY ALERT: September 2025
Critical Risk Calendar As we enter the final weeks of September, corporate security teams must prepare for multiple converging risk events that could impact operations, personnel safety, and business continuity. Here's your essential intelligence briefing for the...

From Reactive to Resilient: Building an Integrated Executive Protection Program for 2025
The Executive Protection Crisis That Changed Everything The assassination of UnitedHealthcare CEO Brian Thompson in December 2024 sent a clear message: traditional executive protection is dangerously outdated. Despite security spending surging over 100% since 2021,...
Quantifying Security Success:
How Data-Driven Metrics Transform Risk Management into Business Value In an era where organizations face evolving threats across both digital and physical domains, security leaders struggle with a fundamental challenge: demonstrating tangible value from investments...

Business Continuity Failures
When Physical Security Business Continuity Plans Fail: The Hidden Crisis Threatening Corporate Operations The Sobering Reality: Most Physical Security Plans Fail When Tested According to ASIS International's 2023 Security Business Index, 75% of security professionals...

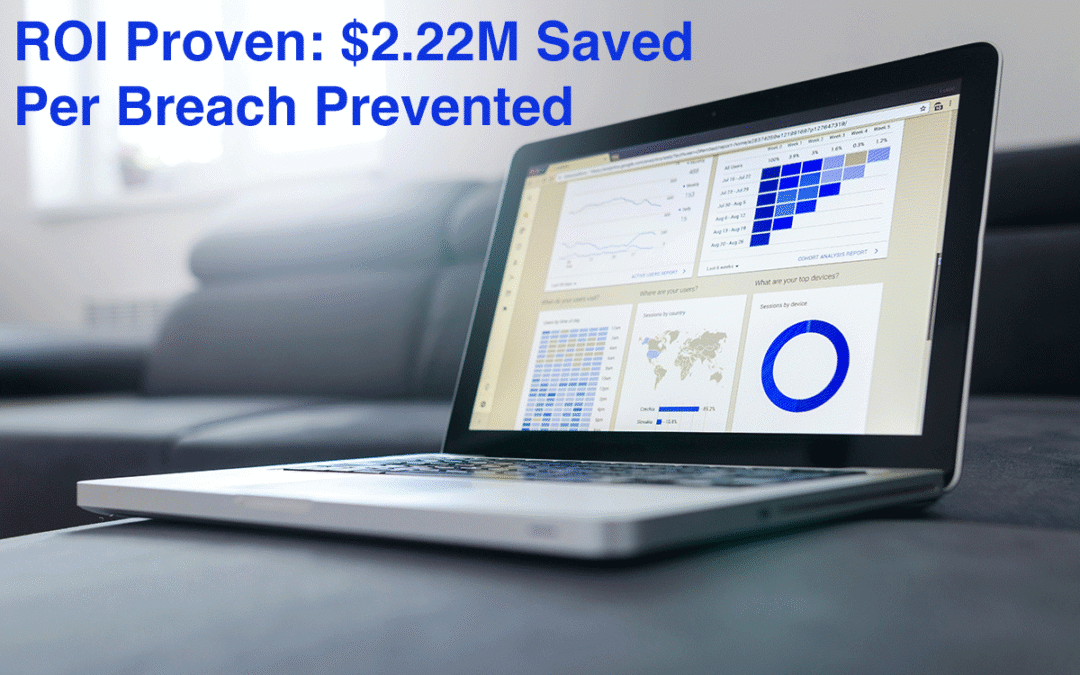
Why Integrated Security Risk Management Saves Organizations $2.22 Million: Lessons from IBM’s 2024 Research
How coordinated incident response across physical and cyber security domains delivers measurable ROI When security incidents strike—whether cyber attacks, physical breaches, or operational disruptions—the difference between a coordinated response and chaos can be...

Bridging the Gaps in Security Management: Top 5 Reasons Security Programs Get Stuck—and What to Do About It
Security incidents are inevitable. But organizational resilience depends less on whether plans exist and more on how well those plans are integrated, tested, and actionable during a crisis The Top 5 Gaps Siloed Risk AssessmentsSecurity risk assessments often sit...

The Cost of Security Incidents in 2025
Did you know that according to IBM's 2024 Cost of a Data Breach Report, the average cost of a data breach reached $4.88 million in 2024, a 10% increase from the previous year IBMI? This figure doesn't even account for the additional costs of damaged reputation, lost...
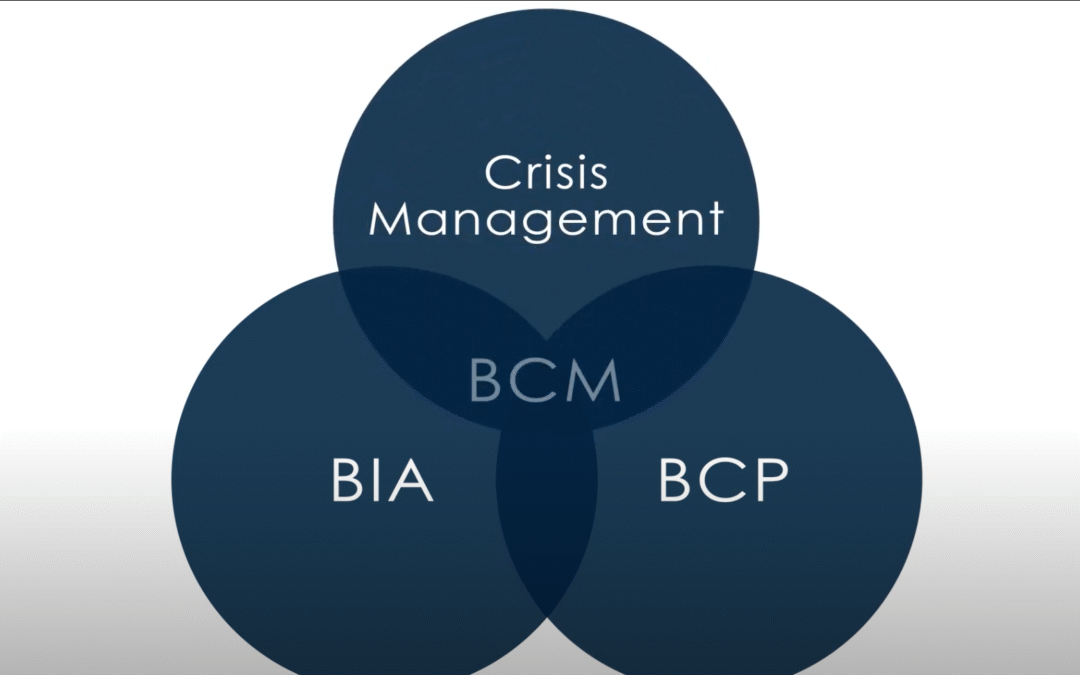
Business Continuity Module
https://youtu.be/SI1sJqHyQlA Business Continuity Management requires extensive planning to ensure your business stays resilient and functioning, despite any potential disruptive events. With our three new BCM modules – Business Impact Analysis, Business Continuity...
